The Future of Operating System Security
It is hard to imagine people nowadays who do not have personal computers, smartphones, or other gadgets. Professional, social, and personal spheres of people’s lives are tightly connected with the Internet. Millions of events happen in cybernetic space daily. As a result, many attacks await a person in cyberspace. Human destinies can break because the computer breaks. A cyberattack can harm your business. A hack like deface can help hackers post fake information on your website or personal social media page. Or they may expose your personal data, photos, videos, or other confidential information. It’s important to protect yourself in cyberspace. Let’s talk about different operating systems that have a high level of protection and will be able to cope with this task in the future.
Popular Operation Systems
The most usually-used OS are MacOS, Windows, Linux, Unikernels, IOS, etc. They share the market and compete to attract new clients.
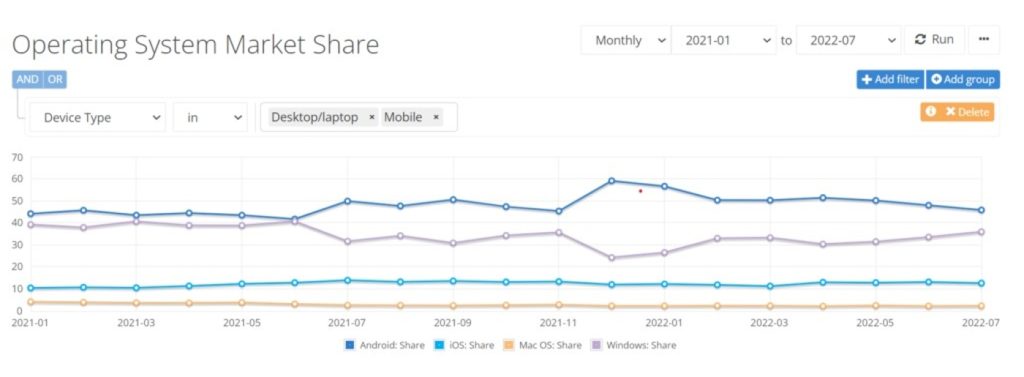
Source: https://netmarketshare.com/
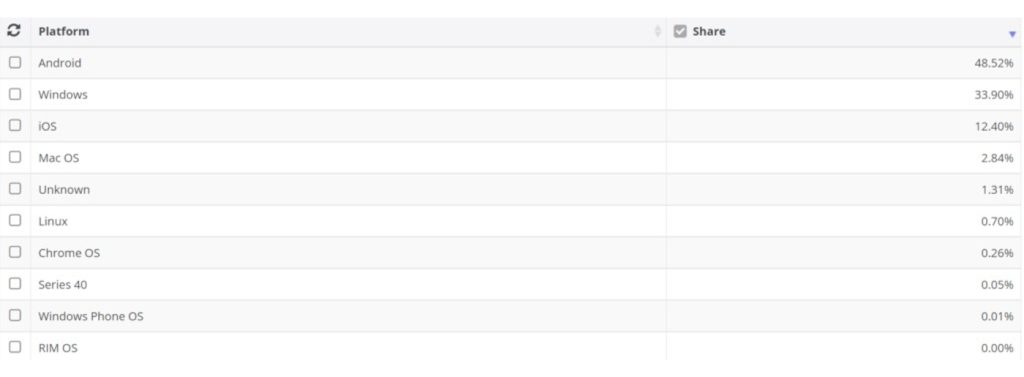
Source: https://netmarketshare.com/
MacOS
The MacOS operating system has become a standard of balance and productivity for many professionals. The history of the operating system began in 1984. Its first version entered the market together with Apple’s first personal computer, the Macintosh. MacOS became a real breakthrough in the field of software development.
The first version of MacOS already had a style that would become Apple’s trademark for many years to come. Since that time, OS developers have been working on new software versions. And they deal with some problems with the new macOS to make it productive and efficient. MacOS protection against malicious software is also worth a special mention. Unlike Windows, on which you can install any program from any source, MacOS supports only programs certified by Apple. This ensures the largest level of security for your data. It also virtually eliminates the possibility of malicious files getting onto your computer.
An Apple computer has built-in protection against most possible cyber threats at the hardware and software level. The risk of data leakage is reduced by 50% for each Mac deployed. It is only important to receive notifications about macOS updates in time. The download will start automatically and without additional payment. Besides, all Mac applications are downloaded from an isolated digital App Store. They undergo rigorous verification there. You can sometimes have macOS update issues, but they are easily solved.
Windows 11
The official release of the operating system took place on October 5, 2021. Security requirements became an important place. To install the current version of Windows, the computer must support TPM 2.0, UEFI, and Secure Boot technologies. The first is required for hardware encryption of information. And the last two are for verifying the authenticity of the software before starting the operating system.
In a typical day, Microsoft processes 65 trillion signals. 2.5 billion is endpoint inquiries. 1,200 password attacks are stopped per second.
What Are the Security Advantages of Windows 11?
- Detection of threats in the early stages
Given the high system requirements of Windows 11, it is logical to ask the question – why are all these measures needed? Microsoft representatives give a comprehensive answer – to protect remote workplaces and corporate servers. They believe that the standard build of Windows 11 will be enough for 80% of enterprises, except the medical, government, banking, and defense sectors. The operating system uses artificial intelligence. It detects phishing links, malicious applications, and threats inside the network. It facilitates the work of system administrators. And it simplifies the construction of the infrastructure of a modern office.
- Hardware and operating system security
Processors compatible with Windows 11 use technologies of virtualization, secure download, and authentication of applications. The operating system itself stores encryption keys and credentials behind extra barriers, making them inaccessible to attackers. The new architecture allows you to grant broad rights to network users without the risk of privacy violations.
- Application security control
Among the supported Windows 11 computer protection tools, it is worth noting:
- multi-level verification of program code;
- protection of component integrity;
- the principle of minimum privileges;
- application isolation.
This makes it possible to defend against attacks from the outside. At the same time, the operating system remains clear and convenient for ordinary users.
- Secured accounts
Since Windows 11 meets the highest criteria for information protection in the segment intended for the user, it introduces passwordless authentication methods. Now they are represented by biometric means – fingerprint scanners and three-dimensional infrared cameras. It is expected that in the future you will be able to sign in to most services with a Microsoft account, just as you can today with social media accounts.
- Cloud services
Part of the Windows 11 image is stored online. These tools check the integrity of the software code and determine the access rights of each application. In addition, they assess the risks when interacting with other devices, be it computers, smartphones, or routers.
Linux
Linux is a server operating system used by every modern company. In ordinary life, it is rarely used by anyone except software engineers, but such well-known systems as Google, Facebook, and Uber work under its control. Linux has been around for more than 30 years, but it continues to be installed on both real computers and virtual machines.
Experts agree that Linux is the most secure OS. This is the most popular OS on servers. A distinctive feature of Linux security is open source. The fact that programmers can read and comment on each other’s code can seem dangerous. But it is not so. The very fact that Linux is open source makes it the most secure OS. Anyone can review the code and make sure there are no bugs or secret tricks – the entire tech community keeps Linux secure. Additionally, Linux users are much less susceptible to spyware and/or any other program that collects user information covertly or deceptively.
Unikernels
Unikernels are designed to make virtual machines more productive and invulnerable to hackers.
Startup NanoVM has developed an operating system for virtual machines called Unikernels, which allows you to abandon Linux from a large number of real computers. The New Atlas website became aware of this project.
Unikernels is a new operating system designed to help computing virtualization and cloud services. The idea is that users don’t need a classic general-purpose operating system like Linux to deploy their software inside a virtual machine. Unikernels makes it easy and simple to run just the application you need, such as an Nginx web server or a MySQL database, as your OS.
This technology provides great security because hackers will not be able to run their malicious software on a virtual machine that is focused on the work of a specific program. The performance also improves: In tests, NanoVM virtual machines have been shown to run common application workloads such as Go web servers 200% faster on Google Cloud, 300% faster on AWS or several seconds less JVM boot time compared to Linux.
Due to the lack of alternatives, IT users had to install a full-fledged OS on “cloud” computers, which can be destroyed with one click of a button. But Unikernels can fundamentally change the situation.
General Recommendations to Feel Secure on the Net

Source: https://unsplash.com/photos/70Rir5vB96U
- Stop using the problematic software until the official announcement of the solution to the problem. Disconnect the computers from the network. It is recommended to reboot the operating system on such computers.
- Ensure the inadmissibility of opening attachments in suspicious or spam messages.
- System administrators and security administrators should pay attention to the filtering of incoming/outgoing information flows, in particular mail and web traffic.
- Change all passwords that function on the network and other identification data that may have been compromised. It is advisable to change the pool of internal IP addresses and the structure of the network. The scheme of the network can be known to attackers, which facilitates the implementation of the next attack.
- To prevent malicious software from changing the MBR, it is recommended to install one of the solutions to prohibit access to the MBR.
- Ensure that all computers have antivirus software installed, functioning properly, and using up-to-date virus signature databases. Install and/or update anti-virus software as needed.
- Obtain Cisco Certified Network Associate certification using ccna exam dumps to identify network vulnerabilities and address cyber threats.
- In case of infection of a personal computer, do not reboot the system.
Conclusion
By 2030, it is anticipated that the size of the global cybersecurity market will increase to 538.3 billion dollars. Thus, many companies develop OS to protect computer information systems, hardware, networks, and data from cyberattacks. The world has seen significant investments in cybersecurity infrastructure. As people become more aware of online hazards.
OS security encompasses many different techniques and methods. They ensure security against threats and attacks. It allows various programs and applications to perform necessary tasks. And it stops unauthorized intrusions. Only you decide which operating system to choose.
In conclusion, we would like to wish cloudless weather over your operating system. And never neglect safety!




Leave a Reply