Email Attack Protection Best Practices and Anti Spam Techniques
The costs of email attacks are devastating for businesses. These costs include financial loss and payout, but also negative branding and reputational harm. The average cost of a spear or phishing incident is upwards of anywhere between $1.6 and $2 million. Part of the reason that this is the place where businesses are vulnerable is that it is up to each individual employee to read and interpret emails to make sure they are legitimate.

Most of the time, large businesses are hacked when a small or medium business that they do business with has been put under an email attack. The cybercriminals use this channel to get to the data of the larger company as well. The types of the breadth of email phishing attacks vary. A few examples from 2018 exemplify the scale of phishing attacks. These include rentals during the World Cup in which people wanted to gain personal information through promising free trips or lodging to the World Cup. Another example is email account takeovers where the behavior of the customer is studied.
Verizon conducted a report and found that about 50 percent of the people who receive a phishing email, actually click on the link. The email attacks lead directly to data breaches and possible identity theft. This spearfishing represents an evolution of email attacks from broad and general to targeted and focused.
Information Gained
Cybercriminals have different reasons for wanting to gain entry into a customer database or other dataset. These include malware, authentication credentials discovery, and corporate information requests.
Malware is a general term for any type of malicious email attack that puts a virus, spyware, or worm on a computer. Authentic credentials discovery is a prime way that the attack happens. The email attack is designed to access databases full of private information. Cybercriminals often want some level of corporate information, including proprietary or patent information. To alleviate this risk, you may want to consider finding identity theft protection.
Email Attack Types

There are many types of email attacks. These are characterized by things such as how they are sent or where they are sent. These include spear phishing, clone phishing, and whaling. Malicious intent can infect a server system in three different ways. These are spoofed communication, malware attachment, and clickbait. To avoid email scams, it is advisable to look up the email address to identify who sent you an email.
Phishing Scam Email Attack
Broadly, phishing scams are those that come from a familiar website or organization and trick people into clicking on them. They typically use messages that stress matters or importance or time-sensitive requests. They often use some existing known information to target certain individuals. For example, they could send bills from a loan company to those who are customers of that loan company.
Spear Phishing Email Attack
Spear phishing is focused on targeting one specific individual or business. The people who use spear-phishing as an attack type are smart. They try as best as they can to trick the recipient into opening the email. There are technologies now that make it hard to differentiate between spear-phishing and a safe email. Cybercriminals are sending personalized email attacks that affect our emotions, such as messages that appear to come from orphanages or pet welfare operations. Oftentimes, the link looks really similar to a legitimate website and it requires careful evaluation.
Whale Phishing Spam
Whale phishing is a subcategory of spear phishing that is aimed at wealthy or powerful individuals. The same tactics used in spear-phishing are also used in whale phishing. The only difference is that whale phishing targets individuals with power or some other level of influence.
Clone Phishing Attack
Clone phishing is another subtype of spear phishing. This takes personalized or targeted phishing to the extreme. It is also known as a spoof email. The cyber-criminal will use a previously sent credible email message and will replace the link with a bad link. The email address appears to be near-identical, but it is a different version than the original email.
All of these phishing and spam email attacks can use images instead of text. They might decide to do this because the anti-spam software and email clients are not as good at detecting bad messages in the form of an image as compared to text.
Anti-Spam Techniques

By now, you know it is up to each employee to successfully decipher and interpret an attempted email attack. No matter how robust your technical training, we are all human, and an employee will undoubtedly open the email and expose the entire system to malware risk. Before using servers and cloud technology, this was an isolated problem. Now, it exposes the whole system quickly to data leakage through the email attack. Email anti-spam is a way to put in automatic deterrents that prevent the email from even reaching the inbox of employees.
There are many types of anti-spam techniques that email clients use to try and thwart spam. The queue system means that a certain number of emails will be successfully sent. After that, a temporary block will be put in place, and the email will not be delivered until after that time limit.
An individual user can decide to block an email address from sending them any mail. This mail is not necessarily spamming but is a commercial message and thus can be declined on a case-by-case basis.
Blacklists
A widespread anti-spam technique is through the use of blacklists. This is accomplished by looking at the IP or domain of someone who is sending spam. These lists can be included in the email administration as a code that blocks emails from these senders. There are several hundred different blacklists.
Greylists
More amorphous than blacklists are greylists. These are similar, but the message is not permanently rejected. After assessing for some level of risk, the message can be sent later. However, if an established number of complaints is reached, then the message will not be sent.
Unsubscribe Email Attack Prevention
In accordance with the anti-spam Act, companies must have their email messages set to be opt-in with an obvious way to unsubscribe from that email. Spamtraps help to stop devious messages that do not follow this rule. They collect email addresses and others from the contact information on websites and begin to send spam messages to these addresses. This spam trap filter identifies those email addresses and prevents the mail from going through.
IP Address
IP addresses are really important when assessing the quality of a message. Each email client has its own internal evaluation system that looks at the IP or range of IP addresses and determines if the message should be blocked or not. Normally, the sender of the email is alerted to this possible blocking.
Anti Spam Server
The most robust and effective anti-spam technique is through the use of an anti-spam server. Companies will use this to filter through every single email message that is sent to an individual with that company. This software is known as an email security appliance. Most of this software will use the above-described techniques before running a more advanced antispam software. Most of these email security appliances are designed this way because it costs money every time an email message is analyzed. By using the existing quality spam checks, the software works efficiently and maximizes the use of resources.
Social Learning
As cybercriminals become smarter, email security appliances also need to become smarter. One of the ways this is being accomplished is through social learning. The systems monitor the behavior of existing email users and treat future messages based on this behavior. For example, if a lot of users mark a message or sender as spam, then the system will learn and mark that message as spam.
This article includes a specific tutorial that helps you learn how to prevent email header injection attacks with PHP.
How to Prevent Email Header Injection Attacks with PHP
This is an advanced-level tutorial, and in this tutorial, you will learn how to place PHP email headers into a web form to prevent malicious spamming or unfiltered user input email attacks and use the results to block scripts if emails are false. There are also steps for creating additional headers to execute a response to email addresses with value.
What are the benefits, and what you will learn from this tutorial?
This tutorial will explain how to build out email headers and create an if/then script to filter out false email addresses while still engaging with true email addresses. When completed, an additional code below will filter out false emails, preventing emails from spamming and protecting online information retrieval.
Why Use Email Headers in PHP?
Creating email headers in PHP is a simple process, but it is easy to miss a few key components that protect emails from header injection on online forms. A poorly written code can lead to stuffed email fields and spam relays. The basics of the code are to create a form that will send an email. The below code is meant to assign values submitted through the post array out to simple variables. The system then builds out an email body and sets up the proper functions to send the message.
<?php
if (isset($_POST[‘send’])) {
$name = $_POST[‘name’];
$email = $_POST[’email’];
$comments = $_POST[‘comments’];
$message = “Name: $name\n”;
$message .= “Email: $email\n”;
$message .= “Comments: $comments”;
mail(‘[email protected]’, ‘Form feedback’, $message, “From: $email”);
}
?>
<!doctype html>
<html lang=”en”>
<head>
<meta charset=”UTF-8″>
<title>Header Injection</title>
<link rel=”stylesheet” href=”styles.css”>
</head>
<body>
<h1>Email Header Injection</h1>
<form action=”form.php” method=”post”>
<p>
<label for=”name”>Name: </label>
<input type=”text” name=”name” id=”name”>
</p>
<p>
<label for=”email”>Email address: </label>
<input type=”email” name=”email” id=”email”>
</p>
<p>
<label for=”comments”>Comments: </label>
<textarea name=”comments” id=”comments”></textarea>
</p>
<p>
<input type=”submit” name=”send” value=”Submit”>
</p>
</form>
</body>
</html>
The next step is where the problem usually lies. Looking at line four, it is evident without correct prevention coding. The fourth argument allows the function to accept multiple headers, opening the door for the aforementioned email address stuffing. Trusting unfiltered user input is dangerous; the best way to ensure the form doesn’t lead to email header injecting is to code and validate the form with PHP correctly.
Validating the Email
Checking email addresses with a regular expression is unquestionably hard. However, PHP’s filer input function makes building this code much more straightforward.
- Start with the above code, and delete the post email $_POST[‘name’] on line four. This part will be assigned to the email variable filter input.
- Still on line four, starting with the post array, type filter_input (INPUT_POST); If using the get array select “INPUT_GET.” The first argument is the kind of input, which is a PHP constant.
- Next, type the second argument in the line, including the name of the field to validate. In this example, the name is “email.” $email = filter_input(INPUT_POST, ’email’, FILTER_VALIDATE_EMAIL);
- Follow ‘email’ by choosing ‘filter to validate email’.
So, your new code from lines 1 to 16 should look like this:
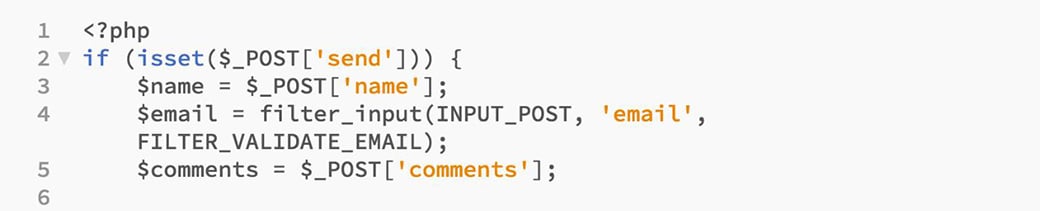
The third argument is the desired method of filtering. There are more PHP constants to use. This will confirm the inserted email is an actual email address and is nothing else besides an email address. If the input information does not return as an email address, it will return as false, and the rest of the functions will not perform.
These additions to the code alone will prevent any email header injection because of the initial false return.
Setting Up the Headers
While the currently updated code is sufficient to protect header injecting, at this stage, it has rendered the function useless, as there is no point in sending out an email to a false return. Build in a conditional script to allow the messaging to execute if the email has value, returning as true. Emails that return false will not run the message.
There is still a small problem in the code. Adding headers is the next step. While it seems intuitive to put a user email address in the form header to allow for a quick and easy reply, this often keeps the form from delivering. If the email address doesn’t match the domain name from the original server, the email will likely bounce. A simple fix is creating a separate header for email replies. This results in two total headers.
- Start on line seven. Place a bracket after the email to create the beginning of the if/then rule. The closing bracket goes at the end of line 12 on line 13.
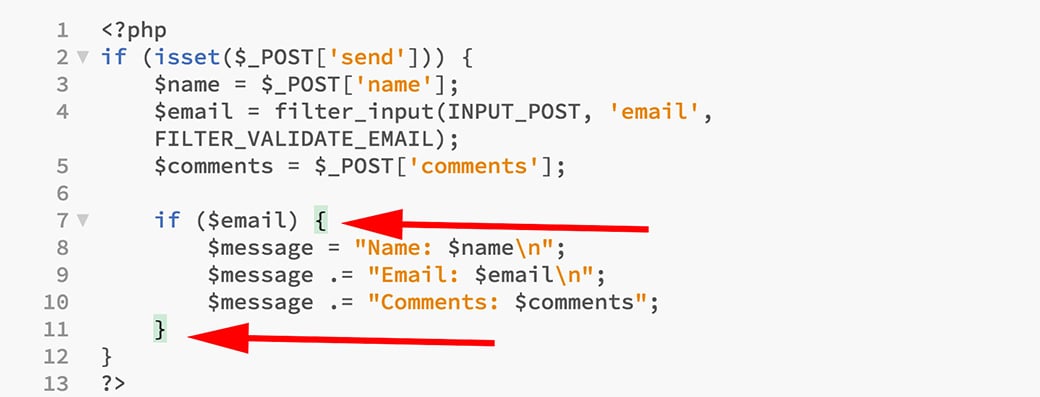
- Add an additional line under line 10 to create the headers.
- Type the following code: $headers = “From: [email protected]\r\nReply-to: $email”; mail(‘[email protected]’, ‘Form feedback’, $message, $headers);
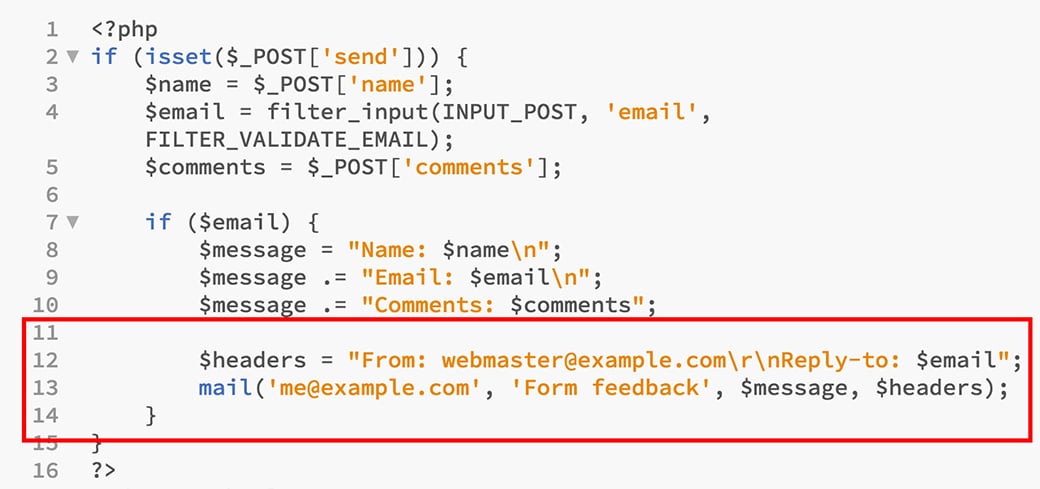
These start with the PHP variable called “headers” and a double-quoted string.
- Using a valid email address from your domain, add the escape sequences and a newline character.
- Finally, add “Reply to” with the email submitted through the form. This makes the fourth argument of the mail function headers.
Your updated code from lines 1 to 16 should look like this:
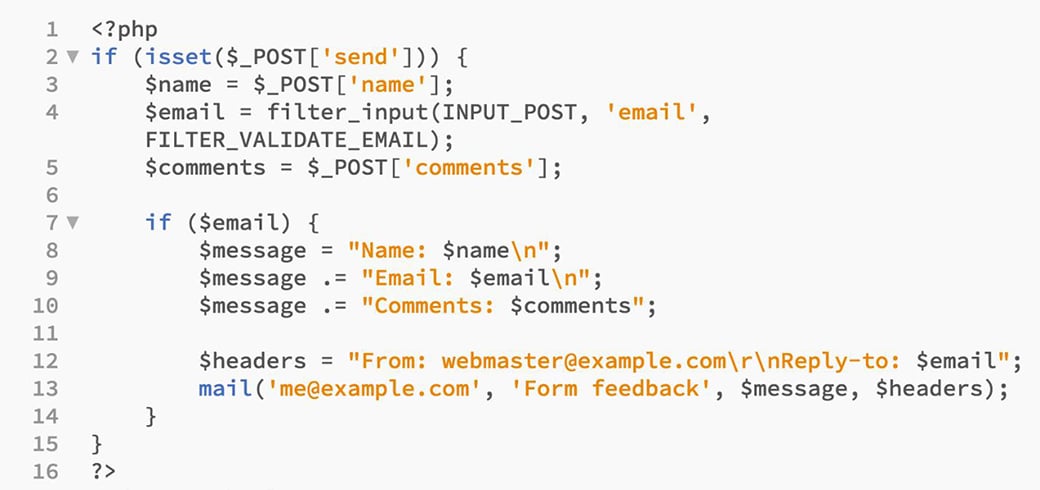
Email Attack Protection – Final Words
It only requires a few lines of well-crafted code to protect a form from email header injections. A few more lines ensure emails travel “To” and “From” headers successfully. Remember, unfiltered user input results open emails up to attacks from malicious users. Validation cannot be done on the browser level, but it must be done at the server level.
PHP is a simple solution to prevent the corruption of input functions. The first and third arguments are PHP constants. The second argument is the string containing the conditions determining if a value is true or false and what actions are taken based on the returned value. The fourth argument provides the necessary protection. Take the time to use PHP to protect your form submissions. It’s worth the effort.
Email Anti-Spam Act
The federal government has established a set of laws for commercial email. These govern the required behavior and features of commercial email messages. If a message does not follow these laws, the company sending the message is at risk of fines.
The law details seven rules that need to be followed. The header information needs to be accurate and identify the business that sent the message. Along with the header information, the subject line must be accurate and descriptive of the message’s contents. If the email message being sent is an advertisement, then it must be disclosed as such. The email must contain a company physical address that identifies where the business is located. An email must show an obvious way to unsubscribe or, in some way, cancel any future messages, and if a customer does request this, it must be honored promptly.
Finally, in the event that a company outsources monitoring of the email or marketing efforts, the company is still responsible for ensuring that the above actions and rules are followed.
Spam Reporting
The federal government also has an email address that can be used to report spam. This is [email protected]. There are also two other ways to report phishing, including at the Federal Trade Commission or at [email protected].




useful and valuable details you shared, thanks for the important blog post. It helped me a lot.