SSL History Changes and Their Influence on the Industry
The year 2017 has seen a lot of changes and events happening in the world of Certificate authority – CA and SSL market. The whole year seemed to be exciting in the SSL history with many advancements and challenges in technology. They made things tough and quite easy to at some point for the developers and techie guys. The companies had a rough time facing these issues and changes that led directly to their business. The whole year round in 2017 there have been month wise changes and events which seem to be prominent enough for your attention. This article will throw some light on these events that will give you a detailed understanding of SSL industry and its growth and advancements.

SSL History of the Year 2017

GoDaddy which is one of the best SSL certificate providers in the market was being forced to revoke the SSL certificates from its around 6000 customers. This happened when the customers discovered a bug in the domain validation system of GoDaddy. Later the company tried to overcome this issue hard by re-issuing the SSL certificate to all its huge chunk of affected customers.
Dead End of SHA1!

This year with this month rolling faced SSL/TLS vulnerabilities and it was followed by the last year challenges of 2016 as well. The year showed the finish of public-trusted SHA-1 SSL/TLS certificates and also a bit more transparency when it came to the issues of certification authorities (CAs). Here the site operators shall make sure that they trust the third-party content coming their way.
Year of the Phish!
In the SSL history, 2017 is considered to be “Year of the Phish”. That’s because the phishing attacks are going to upsurge exponentially in the coming months of 2017. When this phishing will occur on the web pages that will be affected and penalized by Google. These web pages will not encrypt in a severe way so as to elevate the scales of competitive balance and later put them at an extreme disadvantage.
Certificate Transparency Catch Symantec CA for Improper Certs
Encryption is the foundation of SSL industry. So, it is like a web of communications shared via browser and the server. The researchers are trying to make many encrypted apps to use that may ease out the processes and have realized that this helps in securing the recipient’s key messages and data.
For the last two years, the CAs has been continuously supporting CT (Certificate Transparency) logging for all the EV certificates. Later Google announced that CT logging will be needed for all new SSL/TLS certificates this year. On the other hand, one of the founders in SSL industry discovered that there are a total of 108 bad certificates, out of which 9 contained at least one domain which was not validated and the other 99 included a company name which was not validated. This shows Symantec had a bad time and it reduced the trust among its customers which later has to be recovered.
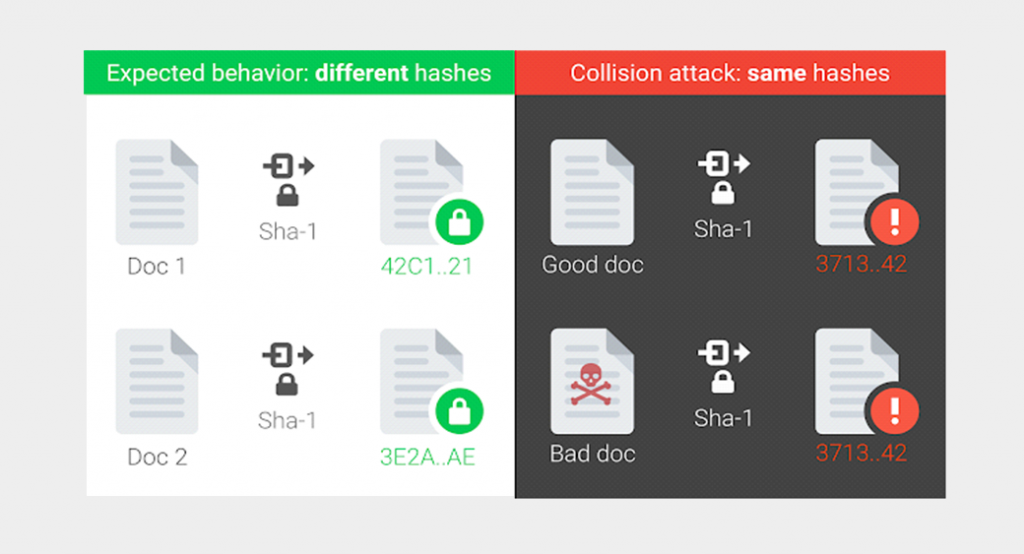
SHA 1 Collision – February 2017
There a rush in the cryptographic hash functions like SHA-1 where you will find hashes are playing a role in browser security, and are also managing code repositories, or can just detect any duplicate files in storage. The cryptographic requirement is always for a wider use, over time, however, this need could fail due to recent attacks on the mathematical underpinnings of these hash functions. Further for all the tech community, the findings in this month emphasized the requirement of the sun setting SHA-1 usage. Later, even Google has supported the deprecation of SHA-1 for many years, predominantly when it comes to signing TLS certificates.
Changes in SSL Certificate Validity
In SSL history it was also necessary to maintain a balance between the data usage with the security and its usability factor. Later a week in this month the Certificate Authority and Browser Forum (CAB Forum) voted on a ballot which made changes to the SSL certificate validity by lessening the lifespan to a maximum of 13 months. It is tremendously questionable but it has to pass out.
CAA Mandated by CA/Browser Forum – March 2017
Certification Authority Authorization (CAA) is specified in RFC 6844 in 2013, which is an official proposal to enhance the strength of the PKI ecosystem. This came with a new and enhanced version to control the issues which CAs has with certificates in particular with the domain name. But they knew this will go to change as the CA/Browser Forum has recently voted to mandate CAA support. What happens is that a CAA creates a DNS mechanism which allows domain name owners to whitelist all the CAs which are permitted to issue certificates for their hostname. For example, example.org. CAA 128 issue “letsencrypt.org”
Symantec Certificates in Trouble
The engineers said that they will roll out the proposal to remove the trust from the old Symantec SSL certificates and the intent to do so is because the validity of the SSL certificates needs to be reduced for a period of newly issued Symantec certificates. This decision came from Google post the conclusion of a research which started on January 19. This also excavated many major problems with Symantec’s certificate issuance process overall.
WoSign & Startcom Certificates Mistrusted
There is an update from Google that in next two months it will conclude the prolonged excommunication which is about the misbehaving of SSL/TLS certificate authorities such as – WoSign and subsidiary StartCom, This came as a punishment announced later this year.
Comodo & Let’s Encrypt Issue Thousands of Certificates for Phishing – April 2017
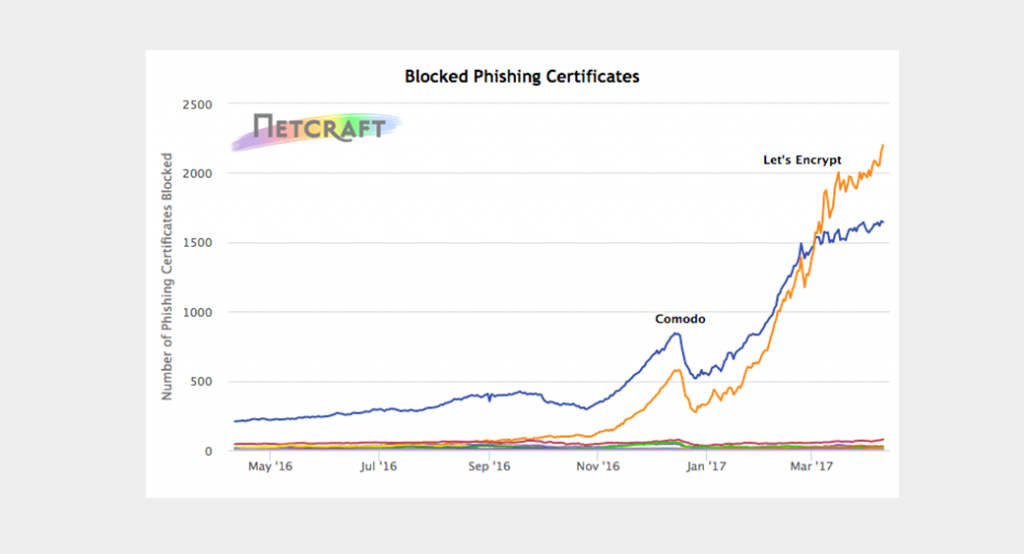
Certificate Authorities are still delivering an immense number of SSL certificates for the domain names and they clearly intended for the use in phishing and fraud. The hackers are frequently using just two CAs, which are Let’s Encrypt and Comodo domain-validated certificates that further account for 96% of phishing sites with an authenticated TLS certificate this year.
Risk Migration & Mitigation Plan
PCI DSS v3.2 agrees that wherever and whenever SSL/Early TLS are used, the Appendix A2 must be entirely completed. The Appendix A2 details are required for the elements of the Risk Migration & Mitigation Plan and also for the migration dates for SSL/Early TLS. These are – it can’t be used for complete implementations, it can’t be used for present implementations after June 30, 2018, and if prior to the June 30, the existing implementations should have a Risk Mitigation & Migration Plan.
Google Completely Distrust WoSign & StartCom Certificates – July 2017
Chrome has started removing the trust factor form the certificates which are issued by the CA WoSign and its subsidiary StartCom. Due to this, there are many incidents that are not matching the high standards expected of Cas. This is one of the most shocking news in SSL history.
Security Doubts on Symantec Certificates
Google will start disbelieving it’s all the current Symantec SSL certificates that start from October 2018. Later Symantec will have to reconstruct the entire certificate issuance procedures from the start in order to remain in the CA (Certificate Authority) business. Later in SSL history, the researchers discovered that Symantec broke the rules and agreed on by the CA/B Forum, which eventually governs the procedures for issuing SSL certificates supported by HTTPS encrypted traffic. This was the final roll for this month in SSL history.
August 2017 – Symanctec Sold Its SSL Unit to Digicert

Symantec has sold its certificate authority (CA) business finally to DigiCert for around US$950 million and also with a 30-per cent stake in the smaller company. This was a new way to resolve the dispute with Symantec. This is the biggest merger in the SSL history.
September 2017 – Chrome Intend to Distrust Symantec Certificates
It was discussed in July well where there were a lot of issues a distrusting the Symantec certificates, in September chrome and the PKI community touched upon a plan to lessen, and eventually remove, trust Symantec’s structure in order to maintain users’ security and privacy when browsing the web.
The security of the Web is one of the most important factors on Google these days. There are many powerful tools in the Web security toolbox that ensures that the connections to the website shall be encrypted via HSTS using HTTPS that eventually prevents the Web traffic from being interrupted, different, or misused in transit.
October 2017 – Google Denounce Chrome Support for HPKP
Google said that HTTP public key pinning will be standardized and now considers the web security to be harmful. But when Google announced the plans to denounce Chrome support for HTTP public key pinning (HPKP), which is an IETF standard then the Google engineers said that this will improve the web security.
December 2017 – TLS 1.3 Update
TLS is the protocol which is behind ‘SSL certificate’ – responsible for encrypted communication and authentication of data. TLS 1.2 is the longest and with all respect to TLS 1.2, now we have TLS 1.3. Currently, it is in testing period but will work soon.
SSL History of the Year 2018
Use of HTTPS Encryption
There is a change coming which is enforced by the Certificate Authority/Browser Forum (CAB Forum) – a regulatory body made up of CAs and Browser. Here the encryption is changing so much, that even if we wait for five years changing the certificates it will be vulnerable and will not help by the time it is renewed. Google publicized that it would strengthen its movement to let the websites use the HTTPS feature by flagging it a not secure tag on the browser. Later in an illustration that websites that do not use HTTPS encryption will get a warning sign. Also, websites with HTTPS algorithm use either the Secure Sockets Layer or (TLS) protocol for encryption.
February 2018 – Biggest Controversy in SSL History Between DigiCert/Trustico
DigiCert has proclaimed that there are plans to revoke more than 23,000 digital certificates which were resold by UK company Trustico in consideration of the allegations of a serious “security incident” at the company. DigiCert responded by mass-revoking but only on the grounds that Trustico will never be stored in its customer’s private keys and other data.
April 2018 – Chrome 66 – Many SSL Certificate are Found Distrust
Chrome 66 has been rolled out for a stable release on all the major platforms. And when it is done it is assumed that it might not be liked by everyone. This is because Google has already dealt with the first blow to the websites which are secured by Symantec. Later when GeoTrust, Symantec, RapidSSL and Thawte SSL certificates were issued somewhere in June 2016 are now totally distrusted by Chrome 66. They say that any other certificates that have been issued between June 2016 and December 2017 have to be re-issued before October 23, 2018.
May 2018 – Google Launched .app Domain with Build in HTTPS

For three years now Google has worked on special applications like app top-level domain. It is the company who is making .app domains. These domains are available to register via Google’s Early Access Program. This TLD has become the best choice for app developers and many other techies in industry. This in-built security safeguard against ad malware, and spying on open Wi-Fi networks.
June 2018 – Track of Changes in HTTP & HTTPS
Whatever happens on the internet has to be tracked and changed. For example, the changes in HTTPS over the last 10 years have made a lot of websites work and switch to HTTPS to protect all their sensitive data and secure transactions. On this note – Chrome’s security UI has emerged in response to the HTTPS use and then later encourages it. It may confuse you at the first but in the long run, they are helpful.
July 2018 – “Not Secure” Without SSL Certificate
Google announced that HTTPS feature is a mandate for the website to imply. The hackers got a threat as now they can’t get into the website very easily. On Feb 2018 Google announced and later in July Chrome 68 released it. Moreover, the website which was not on HTTPS was started getting flagged as non-secure. So don’t lose your customer trust, Get SSL Certificate from the top & cheap SSL certificate providers before July and secure your data.




Leave a Reply